

80% of cyber-attack occurs at application Layer. Stay ahead of attackers with comprehensive penetration testing that identifies vulnerabilities and security weakness. The objective for a web application security testing is to identify exploitable vulnerabilities in applications before hackers are able to exploit them.
View More
In the evolving world of technology, mobile applications are becoming more dominant than ever, this evolution has created a full range of new attacks.
View More
Understand and improve security with vulnerability assessment
Vulnerability assessment can spot the weaknesses in your security defenses before an attacker can exploit them.
Penetration test assesses the effectiveness of security controls by simulating a real-world attack
Penetration Testing involving internal as well as external penetration testing.
Infrastructure security assessment involves identification of the various layers around the application and determining the vulnerabilities/ loopholes existing in them. The tests involve Vulnerability Assessment, Penetration Testing and Network Architecture Reviews. The Open Source Security Testing Methodology Manual (OSSTMM) is adopted for carrying out these tests.
View More
A detailed review of security configurations, based on manual review of configuration settings of assets.
Identifying vulnerabilities on high network and security devices such as High risk user accounts and group configurations, user and group administration / configuration control processes, configuration weaknesses etc.
View More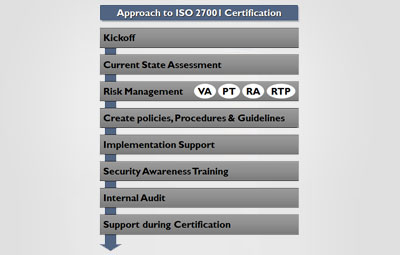
ISO (International Standards Organization) is an independent, non-government for standardization. Information security is the process of protecting information aimed at protecting its availability, privacy and integrity. Effective information security systems incorporate a range of policies, procedures and security products. ISO 27001 is a globally recognised standard against which the Information Security Management System (ISMS) of an organisation can be assessed and certified.
The various phases are Gap analysis against ISO 27001 controls, Risk assessment and management, Technical vulnerability assessment, Information Security Policy and Procedure development, Security awareness sessions, Implementation support, Internal Audit & Support during compliance audit.
amsecure offers expert opinion in challenging cases related to IT, Copyright or Trade Mark across geographical boundaries, even where more than one cyber law exists. We help you address just about any technical aspect of Cyber Law, especially arenas where a single opinion has the power to influence a course of action.
View More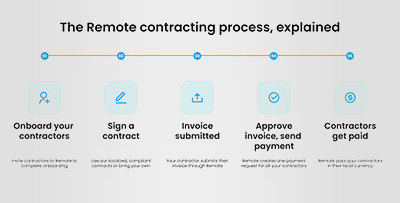
At Amsecure, we recognize the evolving landscape of IT and the demand for skilled professionals without the complexities of traditional employment. Our IT Contractor Services provide a streamlined solution, connecting you with proficient experts from trusted partners.
View More
Our Odoo-based ERP solutions redefine the way businesses operate, providing a seamless and integrated platform to streamline processes and drive growth.
View More